Advanced DDoS Mitigation: An In-Depth Look
 It’s been over two years since Selectel launched its Anti DDoS service, and in that time, over 100 clients have used this service. That comes to over 200 IP addresses and entire /24 subnets.
It’s been over two years since Selectel launched its Anti DDoS service, and in that time, over 100 clients have used this service. That comes to over 200 IP addresses and entire /24 subnets.
Our system has fended off more than 200 major attacks at 10 Gbps, and traffic through the filtration system has grown fivefold. We’ve seen attacks like the Mirai botnet TCP SYN floods, which exceeded 70 Gbps with 17 million packets a second.
Considering the experience we’ve had with DDoS attacks, additional security measures have been taken. For example, we’ve developed unique filtration algorithms that operate up to L7 of the OSI model using behavioral traffic analysis, which creates an algorithm of how actual users work.
When resource consumption is high and availability comes first, we offer an additional level of DDoS protection: Advanced DDoS Mitigation.
Advanced Protection
DDoS attacks can be classified by their target and divided into the following groups:
- Bandwidth exhaustion attacks. This includes UDP floods, ICMP floods (which is a PING flood), and any other case where unsolicited packets are sent. The strength of these attacks is measured in gigabits per second. Attacks are constantly getting bigger and can now be up to 100 Gbps and higher.
- Protocol-level attacks. As the name implies, these attacks exploit the vulnerabilities and restrictions of different network protocols. They bombard the server with parasitic packets, overwhelming the server to the point where it cannot process legitimate users’ requests. An example of this would be SYN floods, teardrop, and other attacks that disrupt the standard circulation of packets within a protocol at different stages.
- Application-level attacks. These disrupt systems by exploiting the vulnerabilities and weaknesses of applications and operating systems. Since these attacks work at up to 1 Kpps, they go unnoticed by standard analyzers. Basic security mitigation measures can’t detect such small traffic flashes, which means traffic needs constant filtering and the systems should know the algorithms behind the actual applications.
Our current mitigation system handles bandwidth exhaustion and protocol-level attacks fairly well.
Advanced DDoS mitigations adds another level of protection to the system: a special proxy server for mitigating attacks on the protocol and application level.
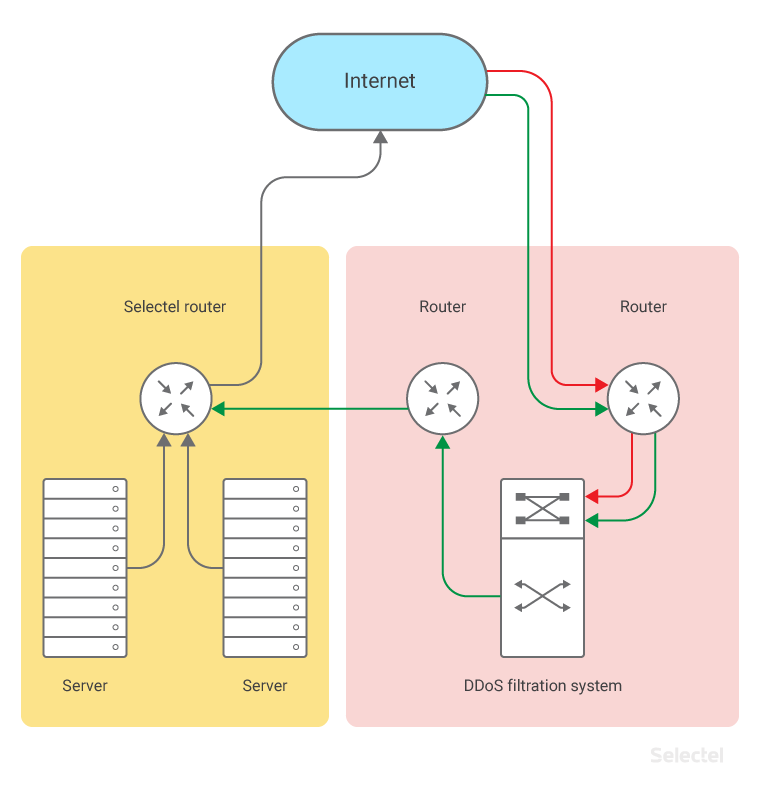
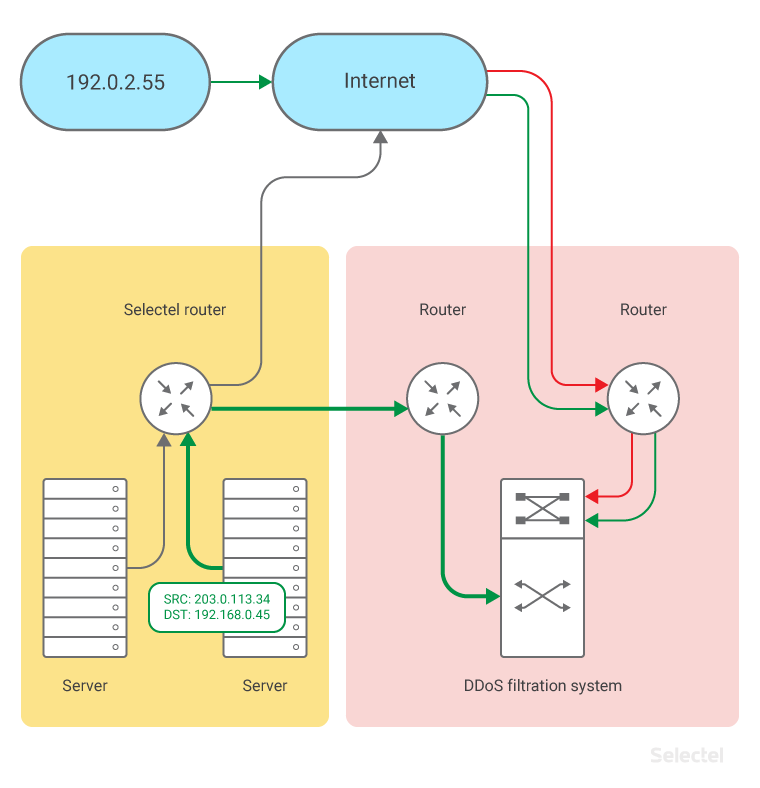
The path filtered traffic takes for our standard Anti DDoS service is shown below:
For Advanced DDoS mitigation, responses from the server also have to be filtered:
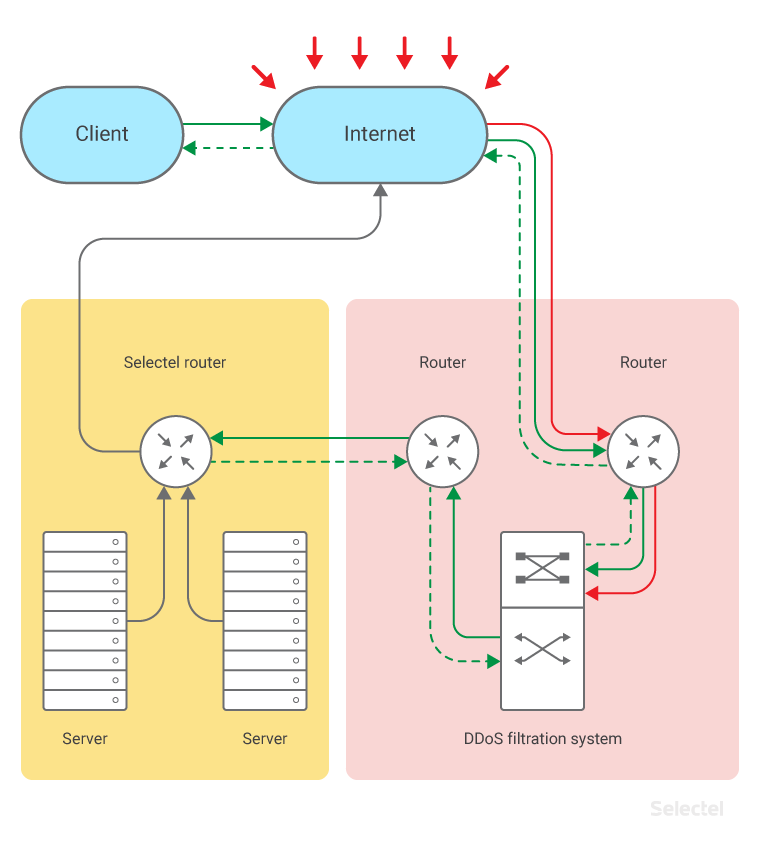
The most basic way to do this is to set up a hardware/software solution that acts as a proxy server on the mitigation side. This would let all data pass through to a protected resource and back.
For HTTP, the proxy server adds the client’s address in the form of an HTTP header (like X-Forwarded-For or X-Real-IP); however, this only works for HTTP-like protocols (HTTP, HTTP/2, HTTPS, Speedy). For other protocols, like those based on TCP and UDP, no headers are added.
How It Works
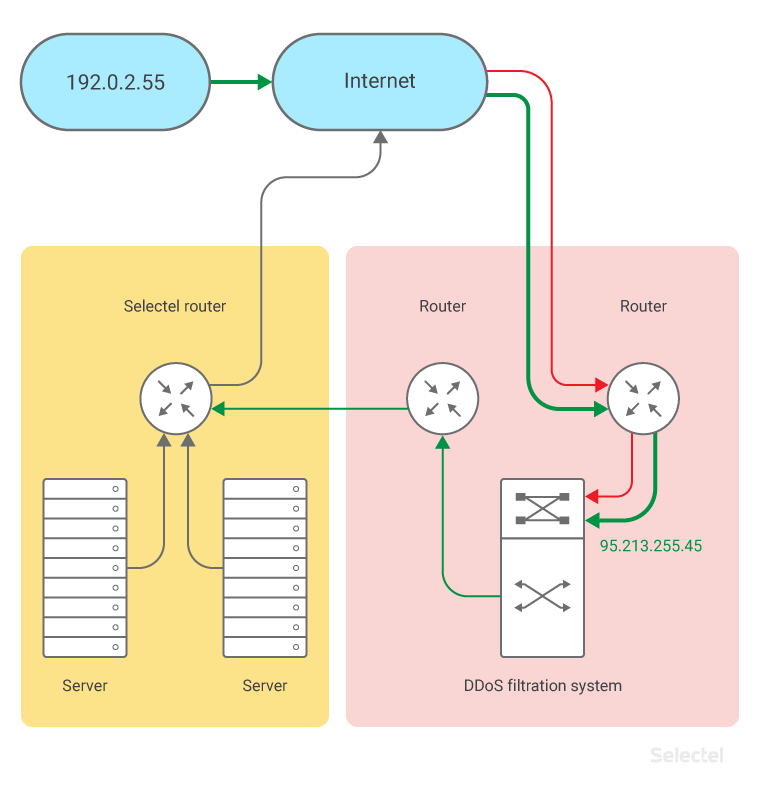
Let’s say the client IP address is 192.0.2.55.
The real IP address of the protected server is 198.51.100.15.
To apply advanced DDoS mitigation to the server, a special questionnaire has to be filled out, indicating which applications on the server need to be protected. The number of applications is the number of objects for projection:
- if there are two applications, then there are two objects
- if one, then one
- if an application has multiple TCP/UDP ports (for example, if this is an SIP proxy, then the application works with both TCP and UDP traffic), this is one application
- if you add a web server, that’s another object. For example, we’ll protect an SIP proxy, which should be available from the Internet as sip.example.ru
Then Selectel allocates a pair of IP addresses:
- 201.0.113.34 – to be set up on the protected server
- 95.213.255.45 – for a proxy service on the mitigation side
The DNS A records for sip.example.ru are made 95.213.255.45.
Client 192.0.2.55 accesses the service by domain and is sent to the IP address 95.213.255.45.
This address can be accessed by routing through the partner network, passing all server traffic from the client through the filtration system.
Traffic is processed in the proxy like this:
What was src-ip 192.0.2.55, dst-ip 95.213.255.45
is now src-ip 192.168.0.45, dst-ip 203.0.113.34; 192.168.0.45 is the address the DDoS mitigation partner uses for NAT pools.
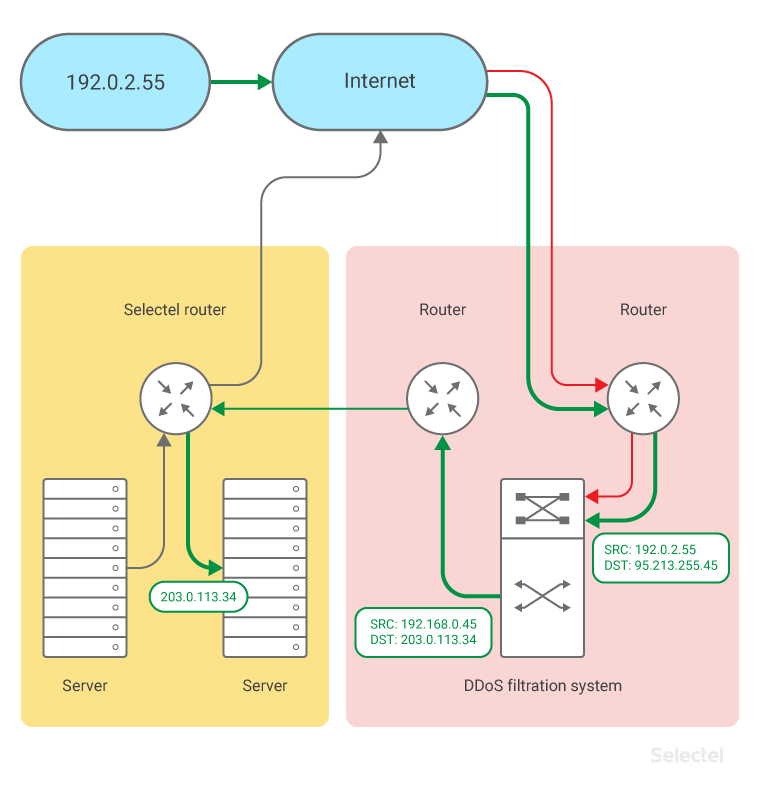
The server’s secure IP, 203.0.113.34, is known only to the server admin, Selectel, and DDoS mitigation partner.
The server’s real address, 198.51.100.15, is used on the server side to organize connections, such as for running apt-get update and performing administration and monitoring over SSH.
The secure (203.0.113.34) and true (198.51.100.15) addresses should be kept secret, as the disclosure of this information would allow hackers to launch a DDoS attack, bypassing the filtration system.
The address 203.0.113.34 connects the server to the traffic filter and doesn’t have a direct Internet connection. To sync the address connecting the server to system filtering traffic to the protected address, Selectel applies static routing, such as:
route 203.0.113.34/32 via 198.51.100.15/.
The server returns traffic over the Internet to the client as follows:
- The server sends an IP packet (src-ip 203.0.113.34, dst-ip 192.168.0.45).
- Traffic from that server to an address like 192.168.0.45 (an address from the traffic filtration system’s NAT pool) is isolated by the Selectel router, which sends the traffic back to the filtration system:
Packets are sent back through the filtration system, where the SRC-IP and DST-IP addresses in the IP packet are replaced. The IP packet is then sent to the client (src-ip 95.213.255.45, dst-ip 192.0.2.55):
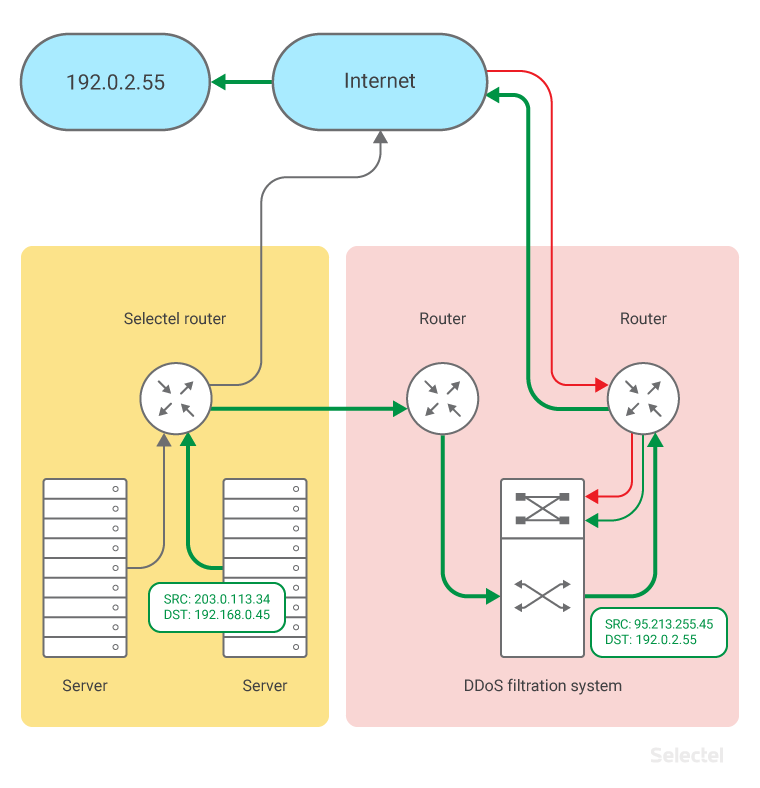
Address transformation is transparent for the client and server. If a device’s address is transferred in packets (usually SIP packets contain the the address of both sides), then ALG processing changes these packets inside the DDoS mitigation system. Today, the system has ALG profiles for FTP, TFTP, SIP, RTSP, PPTP, and IPSec.
Safeguarding Applications
Advanced DDoS Mitigation requires fine tuning. Today, we can offer Advanced DDoS Mitigation for the following applications:
- Web servers (HTTP)
- Encrypted web servers (HTTPS)
- TeamSpeak
- Counter Strike
- Minecraft
- Microsoft RDP
- DNS
If your application isn’t on the list, the system can still be configured manually. Traffic will be analyzed and special algorithms created for your app.
For applications that process protected traffic (HTTPS and other protocols with TSL support), a private key has to be given to the DDoS filtration system to properly establish proxying/web caching. Without this key, application-level mitigation is not possible, and can only be made on the protocol level.
Conclusion
Advanced DDoS Mitigation was developed for HTTP resources, like TeamSpeak, CounterStrike, and DNS.
The system is designed for complete L7 analysis of HTTP traffic packets and can sufficiently handle different kinds of HTTP attacks: XS, SQL-injection, etc.
Both we and our partner need feedback to make our service as effective as possible.
These services can be ordered from the control panel under Networks and Services.