Advanced DDoS Mitigation
 A DDoS attack can cause a company to lose legitimate traffic, or in other words, users. That’s why these attacks are often used as leverage to create unfair competition, and victims often include online shops, games, and e-payment systems.
A DDoS attack can cause a company to lose legitimate traffic, or in other words, users. That’s why these attacks are often used as leverage to create unfair competition, and victims often include online shops, games, and e-payment systems.
Selectel’s Anti DDoS service was launched in 2015 and successfully mitigates the most common attacks, including at the L2 level.
Servers may belong to any of our clients, and we do not place strict restrictions on which IP addresses, configurations, or traffic plans they use. A single rack may host up to 40 different projects, and a DDoS attack may be launched against any one of them at any given time. We fend off 12-20 attacks per day. If a server does go offline, it can be extremely disconcerting and needs to be resolved immediately; this is why every communications channel needs to have a backup.
Attack Types
We can classify the different kinds of attacks by looking at the objective of the attack. The most common kinds of attacks can be divided into four different classes occuring on different OSI-model layers:
| Attack type | Attack objective | Mitigation method |
| First class (L2) | Channel “interference” (Amplification) | Maintain external network access by increasing channel volume |
| Second class (L3) | Disruption of network infrastructure | Advanced analysis of network infrastructure, tracking the problem on passthrough network equipment |
| Third class (L4) | Exploitation of weak points in TCP stack | Analysis of server TCP client and packet behavior, including heuristic analysis |
| Fourth class (L7) | Degradation of web applications (extracting specific information from a database, memory, or disk; depletion of server resources) | Behavioral and correlated analysis, monitoring tools |
Unfortunately, there is no universal solution for DDoS attacks, especially since hackers are constantly on the lookout for new vulnerabilities to exploit.
L2 Example
Let’s take a look at a DNS amplification attack.
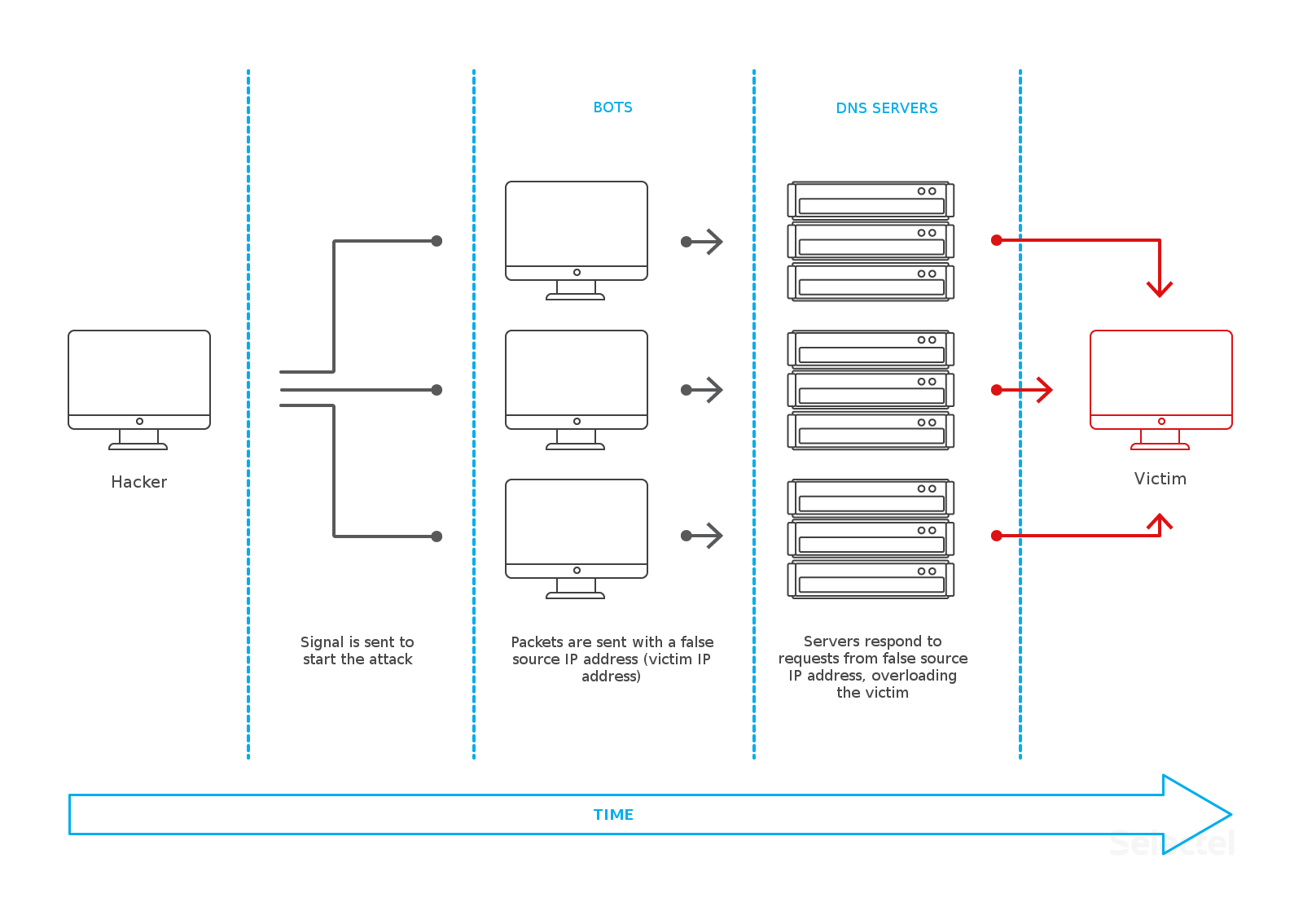
The algorithm for flooding a victim can be summarized as follow: the attacker sends bots the signal to initiate a request cycle to the DNS. All zombified computers start processing requests to their DNS with a false return IP address, which points to the victim computer.
A packet with an IP address should be delivered to the botnet client, but in reality, its enhanced version is sent to the victim’s IP address, which was given earlier.
L3 Example
A classic example of an L3 comes from 2008, when Pakistan erred and captured YouTube prefixes by means of BGP Hijacking, meaning a significant portion of traffic from the videohost was forwarded to Pakistan.
Unfortunately, it’d be impossible to fight off this kind of attack automatically. One must first determine the problem (prefix stealing) happened at all. Then, advanced analysis of the network infrastructure is needed, because generally speaking, the only evidence of hijacking is abnormal network announcing. In other words, to quickly identify hijacking, you need the announcing history.
A Bit of History
Technology is progressing in leaps and bounds, and complex planned attacks (application level, HTTPS) are gaining popularity. This is just what Kaspersky Labs predicted at the end of 2016.
An example of this would be the mixed attack (SYN + TCP connect + HTTP flood + UDP flood) that was launched against the Russian National Electronic Platform. To mitigate such attacks, modern, complex defense mechanisms must be applied.
2nd quarter reports for 2017 with detailed graphs can be viewed here.
DDoS Mitigation Services
As information technology develops and on the backdrop of falling prices for computing resource, base protection is not enough; DDoS attacks are shifting from simple to complex.
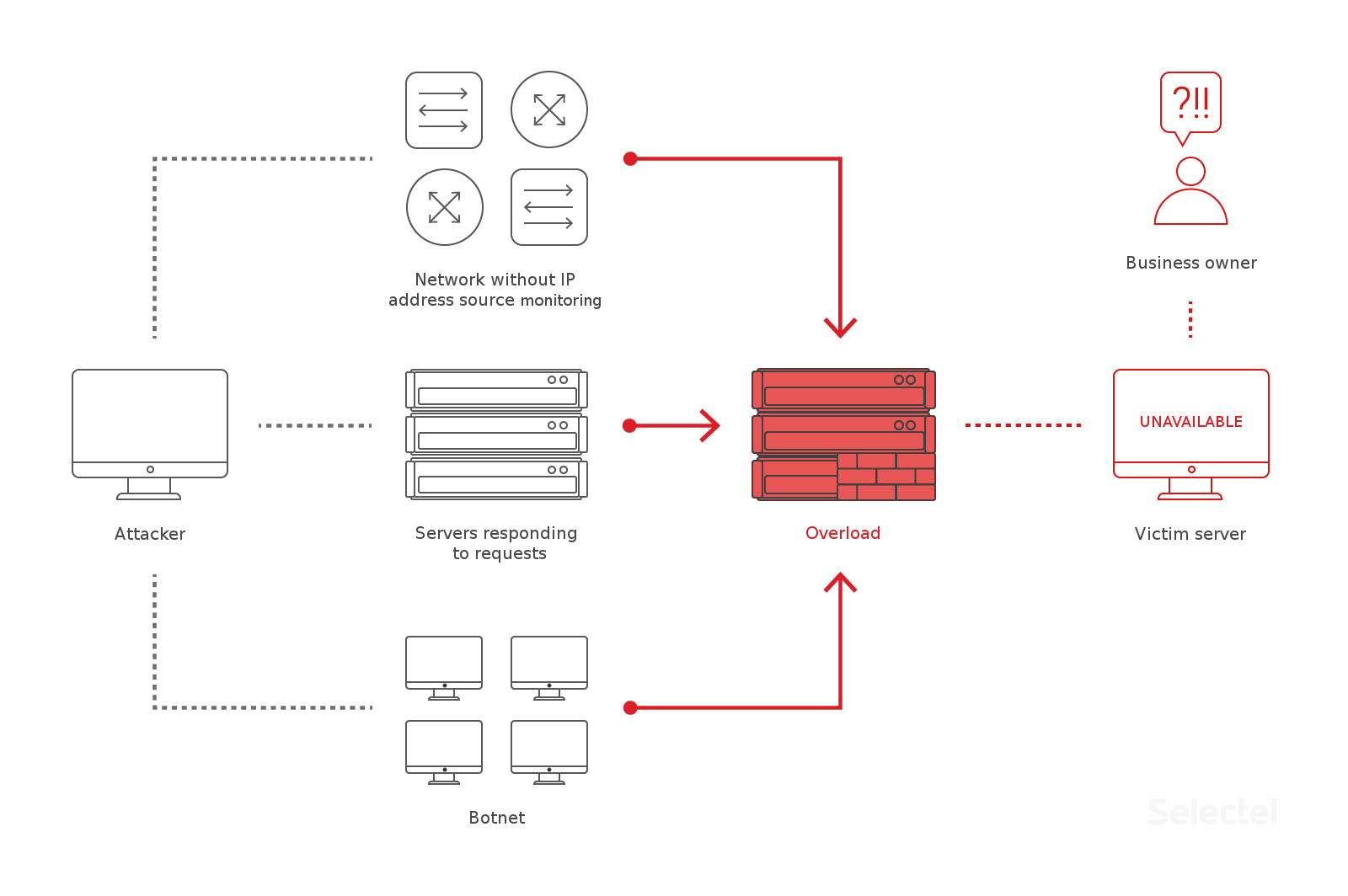
To keep up with this trend, we’ve expanded our professional server and application DDoS mitigation services:
- Base protection – traffic is cleaned by using a protected IP address (one is included in the base fee and additional addresses can be ordered from the Control Panel) and a dedicated communications channel, which dumps all illegitimate traffic. More information about how we clean traffic can be found in our knowledge base.
- Advanced protection – L7 attack mitigation is performed by proxying requests to client applications through a set of filters, where traffic is analyzed and cleaned on the application layer protocols: HTTP, DNS, SIP, game protocols, etc. More information on our advanced protection can be found in our knowledge base.
- Load balancing – Our filters also includes tools for load balancing and raising fault-tolerance. More information can be found in our knowledge base.
Selectel DDoS protection offers the following benefits:
- Pay only for clean incoming traffic
- On-demand access to our filter report system, including information on attack intensity and duration
- Custom mitigation options configured to your project’s requirements
Anti DDoS from Selectel lets you protect your business from financial and reputational losses.
When choosing Advanced DDoS protection, you pay only for the filter connection.
Service costs can be found on the service page.